What Is Phishing?
– T.C., Operations Manager, Property Management
Will You Get Caught in a Phishing Trap?
Phishing is a cybercrime tactic that lures users into clicking bait disguised as something trustworthy, usually within emails. The result often causes the computer to download malware from unprotected or fake websites. The goal of phishing is to glean private information from the user that can either be sold, used in targeted spear phishing attempts, or used to infect the computer or network with malware such as ransomware.
Phishing has many forms and usually, along with malware, results in theft, compromised passwords, and other stolen information, such as the bank account and credit card details of an unsuspecting person.

How Does Phishing Work?
Phishing is generally mass-marketed. A phishing email from a fraudulent email address that is made to mimic a Microsoft service email might be sent to tens of thousands of individuals. At first glance, the spoofed email appears legitimate, and a fair number of people click the link and input their account information, which could be used by or sold to bad actors. Upon closer inspection, the email address often has typos or other spam indicators—instead of the actual email address of the supposed institution, it will have one-off typos, such as the numeral 0 used for a letter o.
For cyber criminals, the appeal of phishing lies in its ratio of effort to reward. Sending a mass-marketed email is easy. Purchasing malware delivery is cheap. And even if many of the email recipients won’t fall for the phishing lure, the handful who do can be extremely lucrative.
What Is a Phishing Email and How Can One Be Recognized?
Phishing also broadly encompasses several different forms of more specialized deception, and each has its own way of betraying its disguise. The examples below are all real-life phishing attempts received by Anderson Technologies’ employees.
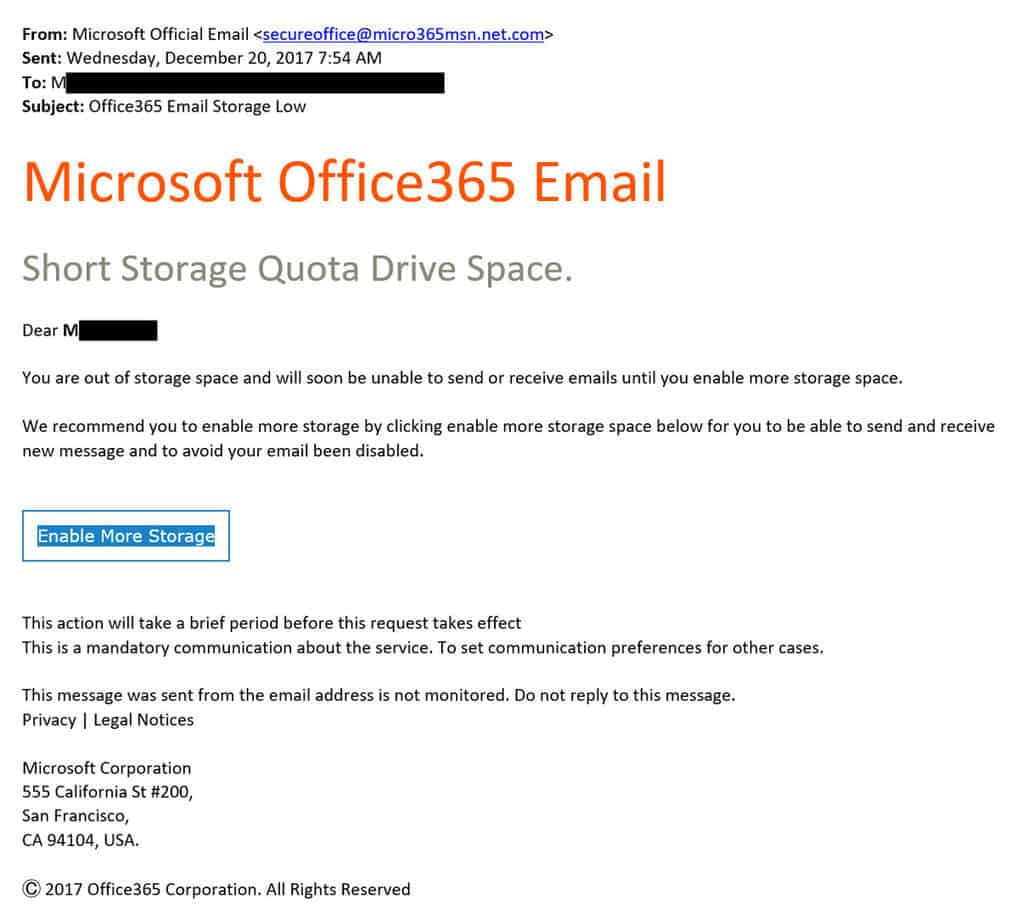
In this example, the phisher knows that the targeted user does utilize a Microsoft Office 365 account. The urgent message—“you… will soon be unable to send or receive emails”—urges the recipient to action. But a quick look at the sender’s email address and the unprofessionally formatted email, indicate that this is a spear phishing attempt and not a legitimate alert. To be reassured, the user could contact Microsoft Office 365 or their IT support directly and check on the status of their storage space.
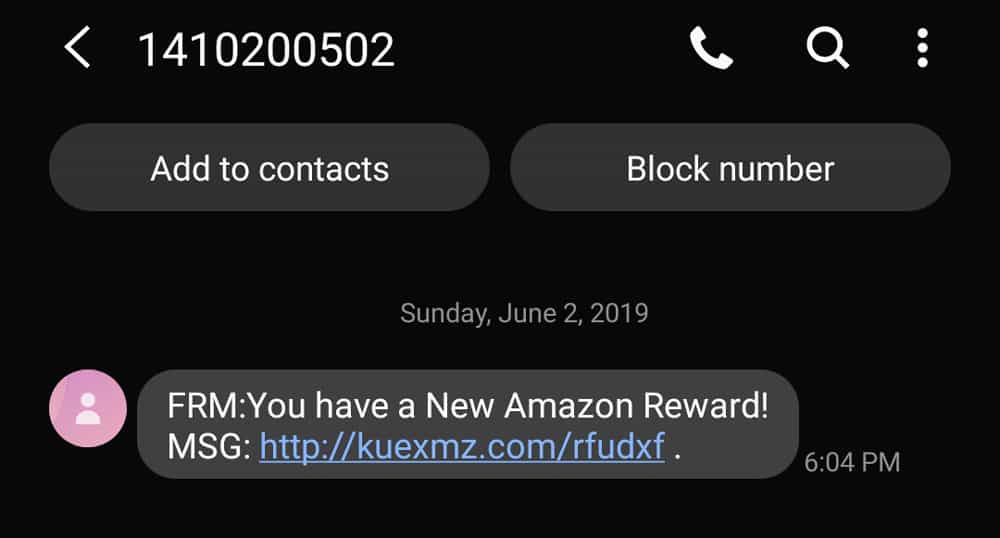
Smishing and vishing are both forms of phishing, but instead of email, they’re delivered through phone services such as SMS and voice calling. Smishing uses text messaging, or SMS, and the user receives a text message asking them for private information or to click a link.
While phone-delivered scams have existed far longer than those sent through email, they remain cheap to produce and lucrative enough to cover operations. Many vishers rely on return customers to fall into their traps. Other smishing and vishing bait are mass-deployed, using auto-generated text and robo-calls to filter out those who won’t take the bait.
A current popular vishing scheme is a robo-call that claims the listener’s social security number is about to be cancelled. For some, this causes enough concern that they provide information and the requested payment.
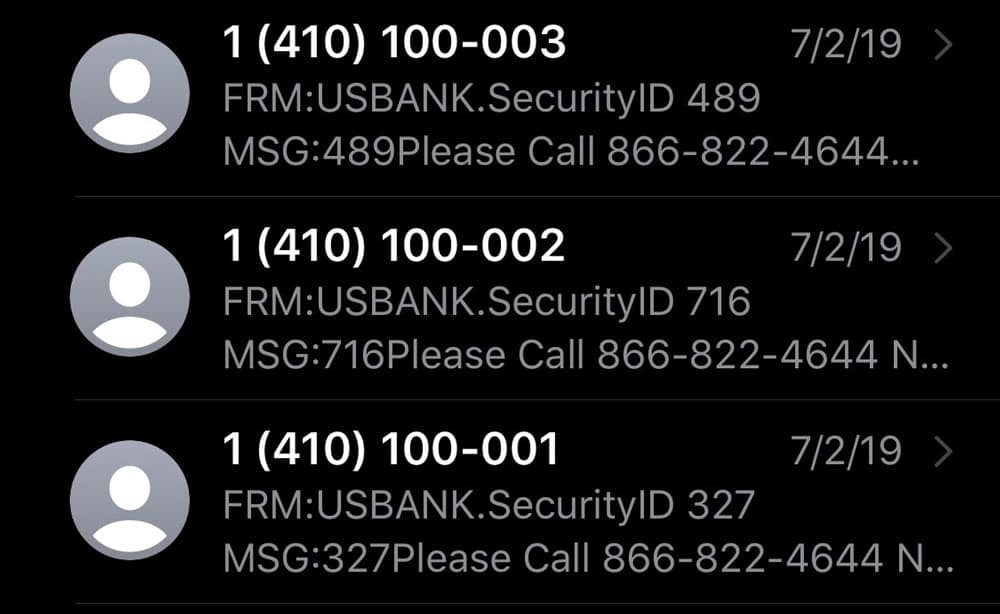
These two examples show mass-deployed smishes. An uninformed user might be enticed by a new Amazon reward, even with an unfamiliar URL attached. And if the user targeted by the second example were a US Bank member, they may have panicked at three security alerts in quick succession and called, revealing their account number to a scammer.
Clone phishing is a man-in-the-middle attack. It intercepts an email you’ve sent that already contains a link and replaces it with a link to a malicious website before sending it out to your contacts as intended. This is especially frustrating because the email comes from your email address, and you don’t even know it’s happened.
Pharming is another form of phishing that doesn’t use a lure. In this case, a user clicks a link and is routed to a bogus website that mirrors the legitimate website asking for personal info. This can happen even in a popular search engine’s results. To prevent this from happening, always check the web address in your browser and verify the “https” in the web address before sharing any private information.
How Can I Prevent Phishing?
Preventing phishing mainly comes in the form of caution and education. Before clicking an email, hover your mouse over the email address and make sure it’s from a real institution. If instead of a .com or other common top-level domain, it has a different country code or a typo in the address that doesn’t make sense for the company, do not touch any link within the email! Especially be skeptical of any message from a source you don’t know that demands payment or claims account closure.
Educate yourself and your employees on the latest threats and commonalities of phishing to prevent biting the bait. The human factor, while our most valuable resource, is also the most liable. People make mistakes, whether unknowingly or because they’re in a hurry. The best thing you can do to protect your business against cyber threats is to educate yourself and your employees.
There are also great email filter tools, such as Proofpoint, which test links before the emails get to your inboxes.
Here are a few more tips to prevent being caught by phishing:
- Never panic and click. The main reason phishing is successful is because it aims to instill a high level of panic in the user, so be vigilant.
- If you don’t recognize the vendor and you didn’t order anything, proceed with caution.
- Never click a link or attachment until you’ve read the entire email and verified the sender’s address. Check for poor grammar or anything that just seems off.
- Use Google. Many phishing scams are extremely widespread, and chances are someone will have reported it.
Could a Hidden Vulnerability be Putting Your Business at Risk?
If you’re not 100% sure, it’s time to find out.
Book your Free Cybersecurity Audit & Plan and get a clear, jargon-free review of your systems, risks, and security gaps. We’ll provide expert insights and a tailored roadmap to help you stay protected and compliant.

