It’s 9:15 AM when your finance director clicks what appears to be a Microsoft security alert. Come 9:17 AM, she’s entered her credentials and 2FA code on what looks exactly like the official login page.
By 9:45 AM, attackers have already accessed her email, set up forwarding rules, downloaded contacts, and initiated fraudulent wire transfers—all while bypassing your company’s two-factor authentication.
The culprit? The Astaroth phishing kit can intercept authentication tokens in real time, rendering traditional security measures ineffective.
In this article, we’ll break down how these attacks work, examine which of the 1.8 billion+ Gmail (and millions more common email services) accounts are most vulnerable, and provide actionable email security tips to keep your business safe from this growing threat.
What Is the Astaroth Phishing Kit?
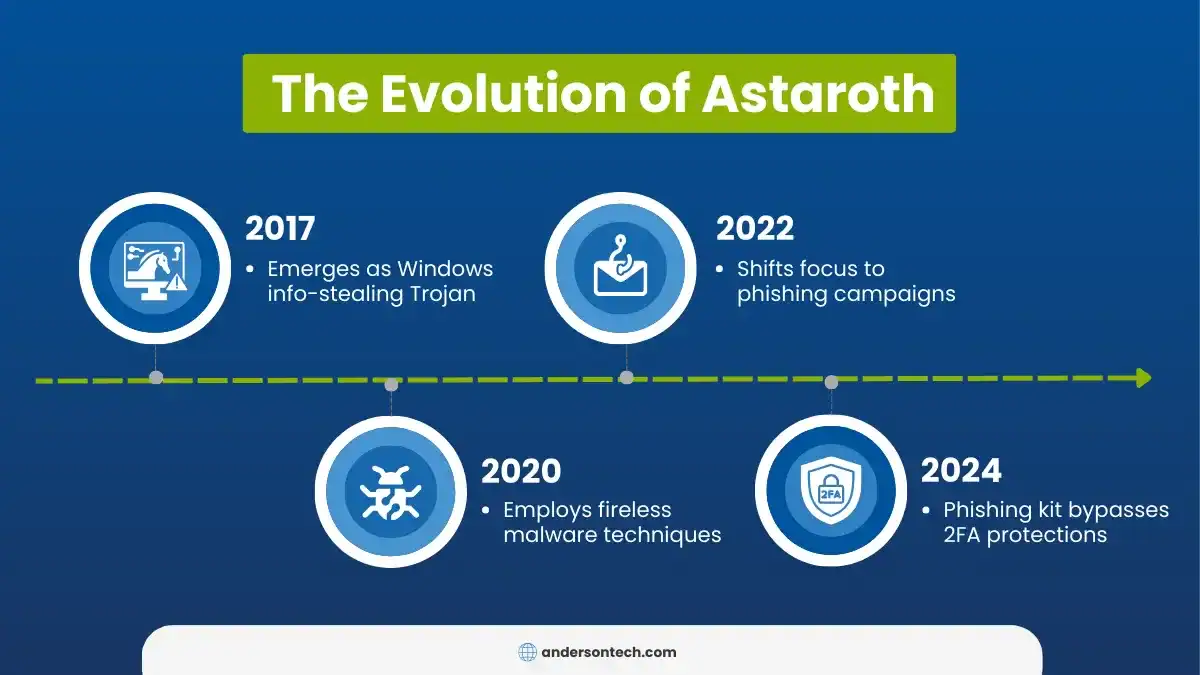
Originally developed as a Windows information-stealer malware in 2017, Astaroth has evolved significantly. Today’s version, first seen in late January 2025, is a comprehensive phishing toolkit that cybercriminals can deploy with minimal technical expertise, making it accessible to a wider range of threat actors.
The modern Astaroth phishing kit creates convincing replicas of legitimate login pages. It uses real-time proxying technology to intercept and steal authentication credentials—including those 2FA tokens you’ve relied on for security thus far.
Unlike its malware predecessor (that needed to be installed on a victim’s computer), this new iteration operates entirely through web browsers. This evolution makes Astaroth business attacks particularly dangerous, as they leave minimal evidence on the victim’s device and can bypass traditional security measures, allowing hackers access to sensitive internal and client data that users assume is adequately protected.
How Astaroth Bypasses 2FA
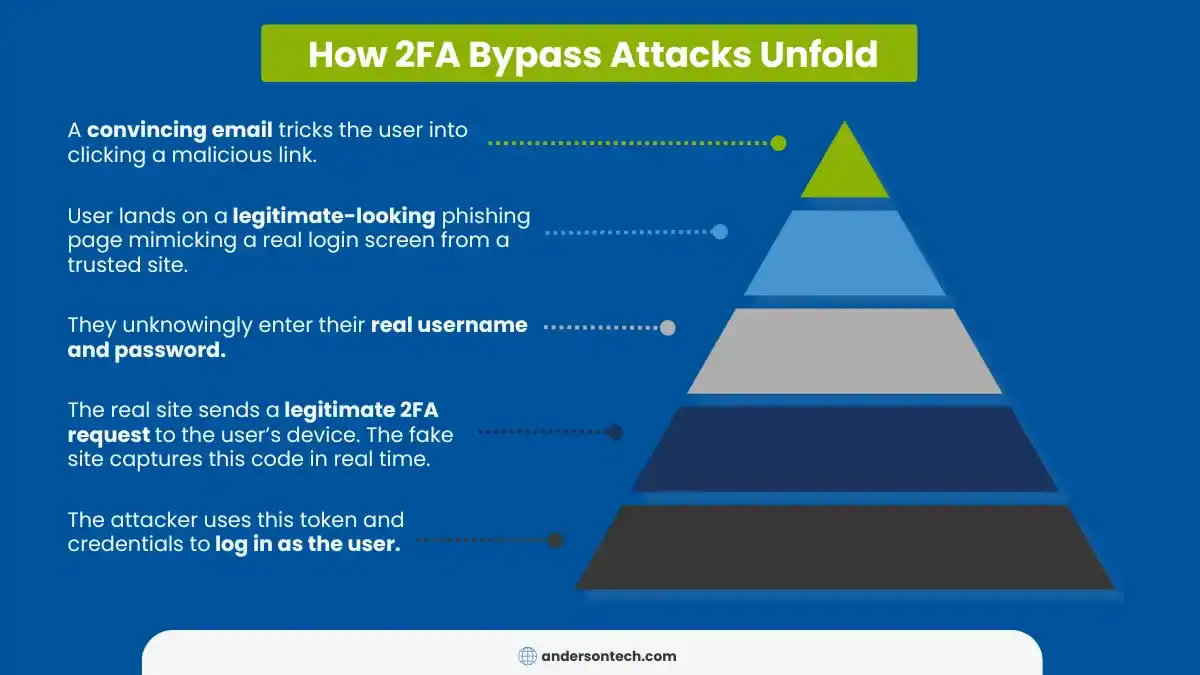
The Astaroth phishing kit’s effectiveness lies in its ability to exploit the user rather than the technology. Here’s how a typical attack unfolds:
Step 1: Initial Contact – The victim receives a convincing phishing email, often mimicking a trusted service like Microsoft 365, Google Workspace, or a financial institution.
Step 2: Credential Harvesting – When the victim clicks the link, they’re directed to a perfect replica of the legitimate login page, where they enter their username and password.
Step 3: Real-Time Proxying – Behind the scenes, the Astaroth kit forwards these credentials to the legitimate site in real time.
Step 4: 2FA Interception – The legitimate site sends a 2FA prompt (whether that’s a code, push notification, or other verification). The victim enters or approves it on the fake site, which the attacker captures and uses immediately.
Step 5: Session Hijacking – With both the primary credentials and 2FA token, the attacker gains full access to the victim’s account while the victim is shown an error message or redirected to the real site.
Instead of exploiting a technical vulnerability in 2FA systems, Astaroth is a sophisticated social engineering attack that turns users like you into an unwitting accomplice. While traditional phishing might just capture static credentials, Astaroth’s real-time proxying means it can capture and use time-sensitive authentication tokens before they expire.
Astaroth in Action: The Real-World Impact of 2FA Bypass Attacks
The Astaroth phishing kit has been observed targeting users of major platforms, including Gmail, Microsoft 365, Yahoo Mail, and various corporate email portals.
For businesses, the implications extend far beyond the initial account compromise:
- Lateral Movement: Once attackers gain access to one account, they often use it to launch internal phishing campaigns that appear even more legitimate. It’s a very successful tactic; why wouldn’t you trust an email from a colleague?
- Credential Stuffing: Compromised credentials are used to attempt access to other services where employees may reuse the same passwords. It’s one of the many reasons we’re so insistent about creating unique login credentials for every business application.
- Data Exfiltration: Sensitive company and client information can be accessed and stolen to be sold on the dark web.
- Financial Fraud: Business email compromise (BEC) can lead to fraudulent wire transfers and payments. An attacker posing as a compromised user might send further, highly targeted emails to their CEO, for example, requesting urgent funds. These would, of course, go straight to the hacker’s bank account instead of the intended recipient.
Why the Astaroth Phishing Kit Is So Effective
The sophistication of the Astaroth phishing kit makes it particularly dangerous. Two factors in particular contribute to its effectiveness:
Psychological Manipulation
Like any social engineering technique, Astaroth business attacks exploit fundamental human psychology:
1. Urgency:
Messages create a sense that immediate action is required
2. Authority:
Emails often appear to come from executives or IT departments
3. Fear:
Warnings about account compromise or security issues trigger emotional responses
4. Familiarity:
Perfect replicas of known brand interfaces lower suspicion
Technical Sophistication
The kit also employs several technical elements that bolster its credibility:
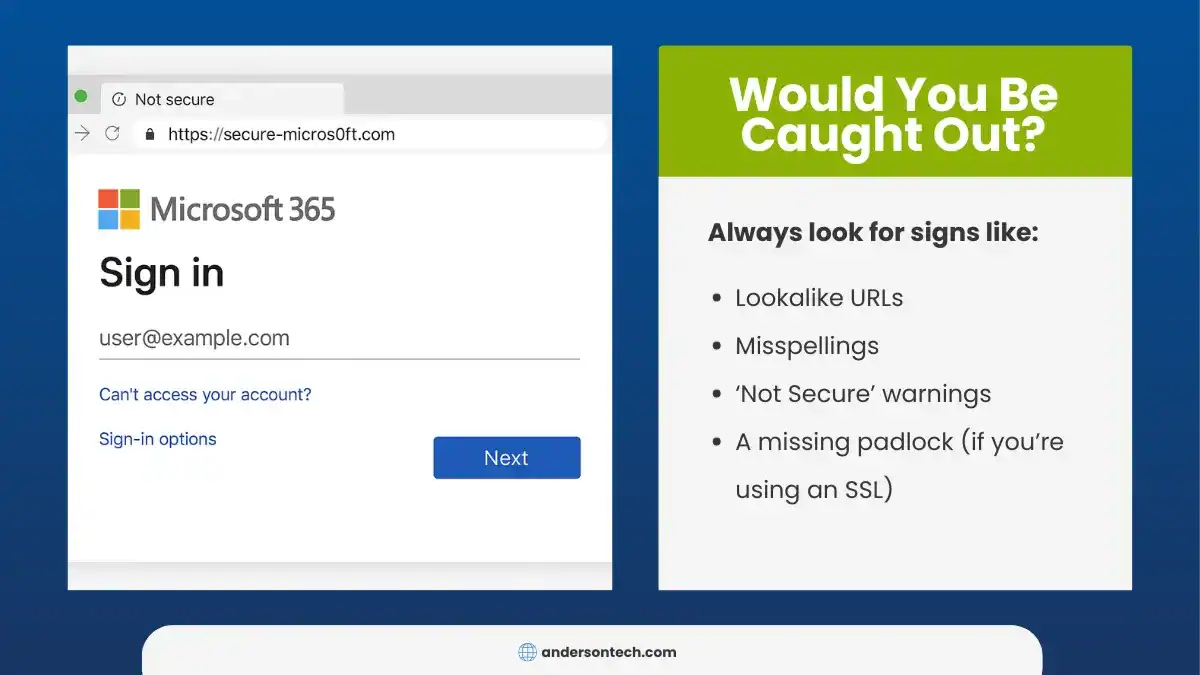
- Valid SSL Certificates: Many phishing pages now display the padlock icon in browsers, falsely signaling security to users
- Mobile-Responsive Design: Pages look legitimate on any device, increasing the attack surface
- Real-Time Interaction: By proxying communication with legitimate services, error messages and responses appear authentic
Who Is Most at Risk from Email Security Threats?
While any organization can fall victim to Astaroth phishing kit attacks, certain sectors and roles face heightened risk.
High-risk industries include:
- Financial services
- Healthcare
- Professional services
- Manufacturing
Small and medium-sized businesses are particularly vulnerable. Though they often lack the sophisticated email security tools and dedicated security personnel of larger enterprises, they still possess valuable data and financial resources that provide a goldmine for attackers.
Role-Based Risk Assessment
Understanding which positions in your organization face the greatest threat can help focus your security efforts. Some of the highest risks are faced by:
Finance Teams: Access to payment systems makes them prime targets for BEC attacks
HR Personnel: Have access to employee data and are often authorized to request sensitive information
IT Administrators: Their elevated system privileges make them valuable targets
C-Suite Executives: High-value targets whose compromised accounts carry significant authority
Customer-Facing Roles: Often have access to customer data and communication channels
Tools like our free guide to Reducing Employee IT Liability are a great starting point for addressing these dangers.
Email Security for Businesses: How to Defend Against Astaroth and Similar Kits
Protection against 2FA bypass attacks requires a multi-layered approach that goes beyond basic security measures:
1. Advanced Email Security Measures
Deploy email security solutions that specifically look for:
- Lookalike domains and brand impersonation
- Newly registered domains in email links
- AI-powered anomaly detection that identifies unusual communication patterns
- Link-time and click-time URL analysis (not just at delivery time)
2. Enhanced User Awareness Training
Standard phishing training isn’t sufficient against Astaroth. Specialized training (like the kind we deliver) focuses on:
- Teaching users to verify website URLs directly, not just look for padlock icons
- Recognizing the signs of real-time phishing (like unexpected authentication requests)
- Establishing verification channels for suspected phishing attempts
- Conducting regular simulated phishing exercises that include 2FA bypass scenarios
Learn more about our one-hour cybersecurity training sessions.
3. Zero Trust Architecture Implementation
Move beyond the assumption that 2FA alone guarantees security. Instead:
- Implement risk-based conditional access policies
- Use device health and location as additional authentication factors
- Apply least-privilege principles to limit damage from compromised accounts
- Enable monitoring for unusual access patterns and behaviors
4. Advanced Technical Controls
Ask your IT team to deploy tools specifically designed to counter advanced phishing:
- Email link sandboxing that evaluates destination sites before allowing user access
- Anti-phishing plugins for browsers that identify suspicious page behaviors
- Token protection (available on Microsoft Entra ID P2 licenses)
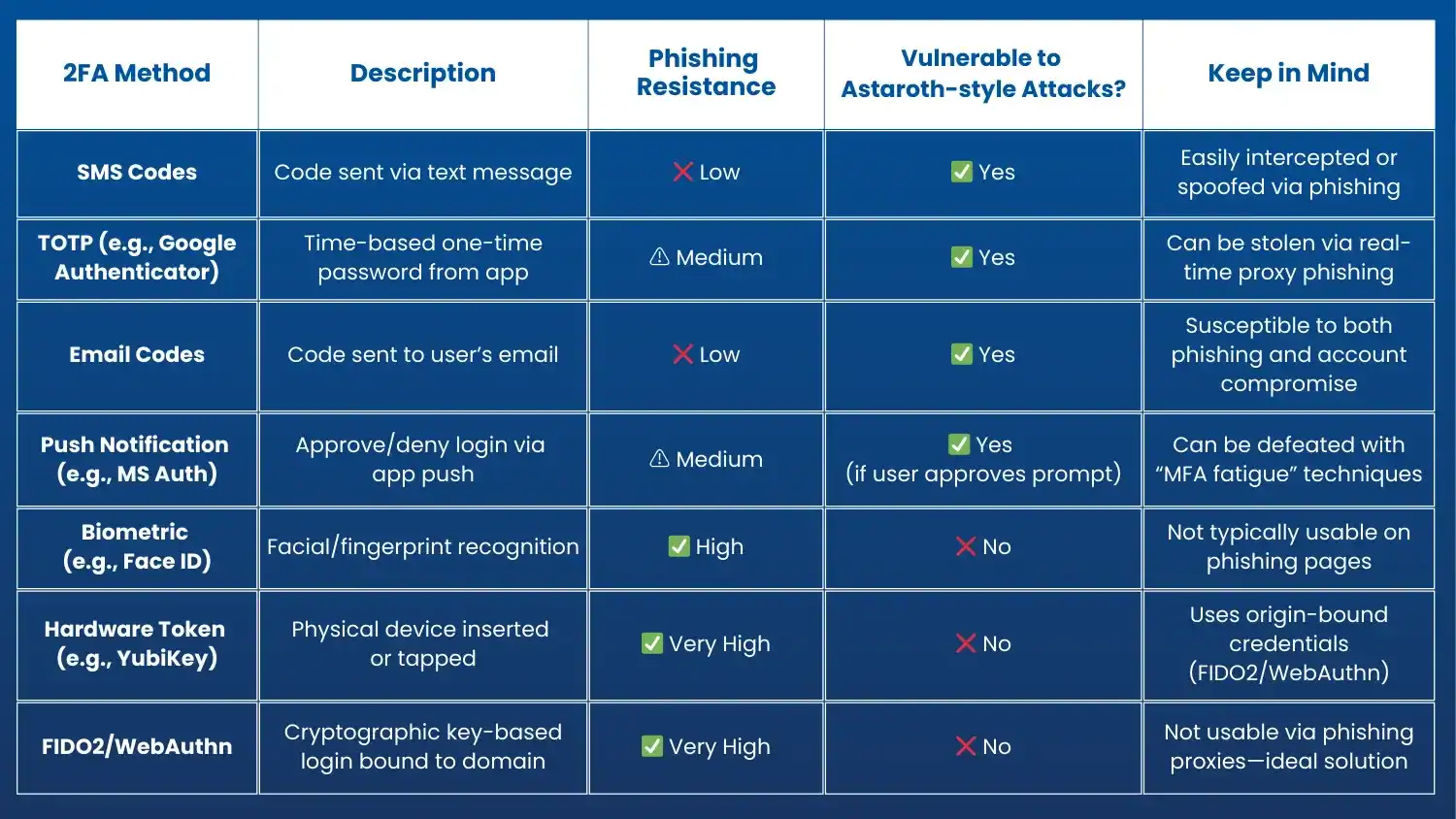
5. Hardware-Based Authentication
Consider stronger authentication methods that resist proxying attacks:
- FIDO2 security keys (like YubiKey or Google Titan)
- Biometric authentication where appropriate
- Certificate-based authentication for critical systems
What the Experts Say
We’re not the first cybersecurity professionals to report on Astaroth—but it’s important to keep iterating the importance of staying vigilant against evolving phishing threats.
In British news outlet The Daily Mail, cybersecurity expert James Knight advised that just because an email looks like a Gmail or Office login doesn’t mean it is:
“If these emails are received, people should be very careful what they open and the links they click on.”
Responsibility doesn’t just fall on the individual. Bank Info Security reported SlashNet’s Field CTO, J. Stephen Kowski’s advice for IT departments:
“Security teams should use fast, real-time threat detection across web, email, and mobile channels while also teaching users to spot fake pages.”
Across the board, the expert advice is the same:
- Train all staff to be vigilant
- Always check your emails for signs of phishing (like urgency, spelling and grammar errors, or inconsistent sender addresses)
- If in doubt, don’t click the link.
Actionable Email Security Tips to Implement Today
You don’t need to wait to improve your protection against Astaroth and similar threats. Immediate steps you can take include:
- Audit your current 2FA implementation and consider supplementing with additional verification factors
- Reviewing your incident response plan to ensure it includes procedures for account compromise despite 2FA
- Implementing automated alerts for unusual login activities, especially from new locations or devices
- Creating a simple verification procedure for financial transactions or sensitive data requests
- Training employees to use password managers. This will reduce password reuse across services, minimizing the potential impact of account compromise.
Key Takeaways
So, to summarize everything you’ve learned today:
What is Astaroth?
Astaroth is a trick tool that hackers use to make fake websites that look just like real login pages. When you type your password and security code into these fake pages, the hackers can steal them and break into your accounts.
Why is Astaroth dangerous?
Astaroth is dangerous because it can bypass 2FA protection—which many users rely on as a primary security measure. It also operates without leaving evidence on victims’ devices and enables attackers to gain complete access to business accounts with a high success rate.
How do I protect my business from 2FA bypass attacks?
Protect your business by implementing layered cybersecurity solutions, including advanced user awareness training, hardware-based authentication (like FIDO2 security keys), zero trust architecture, sophisticated email filtering, and establishing verification procedures for sensitive requests.
Who Is Anderson Technologies?
For over 30 years, Anderson Technologies has specialized in providing comprehensive IT and cybersecurity solutions to businesses in St. Louis and beyond.
Our team of certified security experts can help protect your organization from sophisticated threats like the Astaroth phishing kit through advanced email security implementations, custom security awareness training, and proactive monitoring services.
Get Cybersecurity in St. Louis and Beyond
Whether you’re an existing client looking to strengthen your overall defenses or a business seeking expert guidance on email security, we offer personalized solutions tailored to your specific needs and industry requirements.
Schedule a free IT security risk assessment to get a taste of what we offer and start protecting your business today.



