The Top Mobile Security Threats
– T.C., Operations Manager, Property Management
Is Your Mobile Device Secure?
Working from home? Providing mobile options for your workforce? Or just want to make sure your personal device is secure? You’ve come to the right place.
Even before the unprecedented shift to working from home in early 2020, increased usage of laptops, tablets, and smart phones for business and organizational applications has increased the number of attacks designed for and focused on mobile devices. Mobile devices, now more than ever, contain business-critical, sensitive, and confidential data.
- 1. Phishing and SMSishing
- 2. BYOD (Bring Your Own Device)
- 3. Malicious Apps
- 4. Data Leakage
- 5. Network Connections

1. Phishing and SMSishing
Phishing
While successful phishing attacks are decreasing thanks to email filtering and comprehensive employee education, phishing attacks on mobile devices continue to be a persistent threat. In fact, users are more likely to fall for phishing on mobile devices, especially phones and tablets, due in part to the inherently simplistic design.
Mobile apps are created to streamline the available information for use on smaller screens. Unfortunately, much of the information that is not available on mobile apps is the information necessary to determine the authenticity of an email or website. Most email applications display the sender’s name, which can be falsified, and not the full email address, which could identify a problem. It’s also more difficult to identify the security of a webpage on a mobile device versus a desktop or laptop browser.
Mobile software also enhances the prominence of GUI elements that foster action—accept, reply, send, like, and such—which make it easier for users to respond to a request. Thus, on the one hand, the hardware and software on mobile devices restrict the quality of information that is available, while on the other they make it easier for users to make snap decisions.”— Verizon’s 2019 Data Breach Investigations Report
Add in the distractions of everyday life when using a mobile device, and you have a perfect storm of conditions to click that bad link or open that malicious attachment. It is up to the user to maintain their skepticism while using a mobile device and avoid opening any email or clicking any link, even from a trusted contact, unless you can verify that they sent it. That may mean waiting to deal with an email until you are on your primary computer.
SMSishing
SMSishing is a specialized type of phishing that uses text messages to lure people into clicking a link. Besides the method of communication, the biggest difference between phishing and SMSishing is the style of the lure. These are not the targeted or well-crafted emails lures that mimic real companies. SMSishing attempts are usually generic, with no real attempt at targeting individuals or groups. Often, they appear as threats or offers that the recipient will lose something or miss an opportunity for free items if they do not click the link provided.
SMSishing attempts go out of their way not to mimic a specific company or website, so that they can be sent to as many people as possible. If they used a specific company that the recipient doesn’t work with or purchase from, the number of people they can trick into clicking goes down.
You should always be suspicious of a link sent over text message. If it is from a known contact, call them and make sure they intended to send the link. If there are no clear indicators of who or what company the message is from, do not click the link.
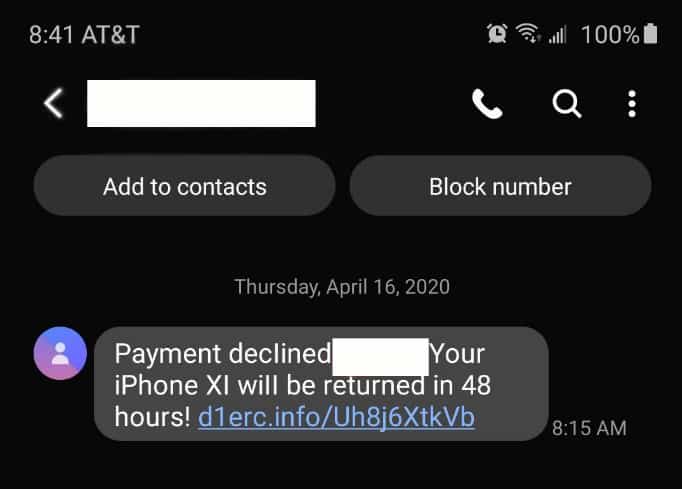
Specialized Phishing and SMSishing Campaigns
Criminals always take advantage of events that affect a large group of people. Many scammers temporarily change tactics around tax time to trick people who may be anxious or confused by their filing. A key to getting people to click is to override their better judgement with fear tactics or an enticing reward. The COVID-19 coronavirus is another event that scammers are using to scare and confuse people into clicking.
2. BYOD (Bring Your Own Device)
Bring your own device (BYOD) refers to employees using personal mobile devices (phones, tablets) to access company data for work. Often, this is limited to checking email, but with more people working from home, mobile access is growing and with it grows the danger to your data. BYODs rarely have the same level of security protections in place as a company owned and managed device.
Most personal devices do not enable encryption, nor do they restrict app usage or run anti-virus/malware software. If the device is older, it may not even receive new operating system updates for known vulnerabilities. If lost or stolen, few users have the ability to locate the device or remotely wipe all data from it if it is irretrievable. All of these factors make for dangerous cyber security conditions.
The best option for BYODs is to limit access to company data. Use only single function applications like an email service or messaging app. This keeps any potential danger isolated from the rest of your company’s data.
3. Malicious Apps
A malicious app is an app that appears to be a legitimate app but, once downloaded, turns out to be infected with malware or spyware. Malicious apps are a danger but also avoidable if you and your employees take proper precautions.
Malicious apps are often found in non-official app stores, and when in an official app store, it is usually free and by a no-name developer. (The Apple App Store has more security measures in place compared to the Google Play Store, but neither is 100% free of malicious apps.)
The best way to protect yourself from malicious apps is to always get apps from an official app store. Avoid apps from developers you don’t know or cannot find any information on, and check the comments to make sure people haven’t warned of danger. If your employees use a company device, restrict their ability to download apps that are not approved for work.
4. Data Leakage
The greater danger from apps, however, is not in downloading a malicious one, but in allowing legitimate, functional apps too many permissions. These permissions may compromise the security of your company through data leakage.
When you download an app, the first time you use it, it asks for certain permissions. Do you look at these permissions every time? Do you understand what kind of access that permission gives the app? Many people inadvertently give apps far more permissions to their mobile device than the app actually needs.
Permissions are the access privileges that an app needs in order to function as designed. A permission for a camera app might include Access to Internal Storage in order to save any captured images. Such a permission make sense for the purpose of the app. That same permission makes far less sense for a weather app.
Many apps ask for a wide range of permissions, some that don’t involve the functionality of the app at all. Developers often do this to gather data from the phone, such as usage information, location data, or even photos and emails located on the phone. Once collected, this information can be sold or used internally without you knowing. If you have sensitive or private information or pictures on your phone, these can be siphoned off as well.
It’s important to remain vigilant when granting an app’s permissions. If they provide an explanation for why the permission is necessary, consider if that seems reasonable or if that’s too much to risk. See if you can reject any permissions you don’t agree with. Some apps allow this, but unfortunately most require you to accept all permissions in order to use the app.
In order to protect your security, refuse to use any app that asks for permissions it doesn’t need or you don’t agree with.
If you wouldn’t allow a person to access the information on your mobile device, don’t allow an app to.
5. Network Connections
One of the reasons to use mobile devices for work is the ability to work from wherever you are, but that freedom comes with risks. When not in the office or at home, public Wi-Fi is a convenient way to avoid using too much cellular data. This is fine for playing online games or streaming video or music, but when it comes to work or accessing any other sensitive data, public Wi-Fi should be avoided.
Bad actors can easily extract any data sent over unsecured Wi-Fi without you being the wiser. You may not even end up on the network you thought you were joining. Network spoofing happens when someone sets up a Wi-Fi network to appear as if it is the network of a legitimate business, such as setting up a network named “Coffeehouse” within range of an actual coffee house.
Secured public Wi-Fi is not as protected as you may expect, either. Though the bad actor scanning for open networks won’t be a problem, if the password is freely given to visitors and patrons, a bad actor can login to the Wi-Fi, making it no safer to use than an unsecured network.
What can you do to protect your data when working on the go? Never use public Wi-Fi for sensitive communications or transmissions, not even logging into an application or website. Log-in credentials are as good as the data itself. If you need to use public Wi-Fi for business, use a VPN to ensure your data is encrypted. The best option would be a VPN that connects to your business directly, but a commercial VPN service will work as well.
Threats are ever changing, but you can rely on Anderson Technologies to keep up with current cybersecurity trends to help our clients stay one step ahead of the criminals. If you need help securing your mobile devices, contact Anderson Technologies today at 314-394-3001 or info@andersontech.com.
A Free IT Assessment Can Help You Identify Risks
Your organization is too valuable to not have modern IT systems to keep it safe and make it scalable. A free Anderson Technologies IT Assessment will identify where you are the most vulnerable and recommend the areas to address first, affording you the most protection and peace of mind.




