In part 4 of our HIPAA series, we dug deep into the Security Risk Analysis (SRA) and how to perform one. This time, we’re going to look at what to do with the SRA once it’s completed. The SRA serves as a starting point for fulfilling many of the standards of the Security Rule, but its most important function is to help you create a risk management plan to mitigate and monitor the risks you identified. The risk management plan will determine what actual changes you make to ensure your electronic protected health information (ePHI) and your business are safe from all reasonably anticipated threats.
What is a Risk Management Plan?
In the SRA, risk is identified, current security measures are evaluated, and the potential impact of a vulnerability being exploited/triggered is determined. A risk management plan takes all that information and turns it into a plan of action. It prioritizes the risks with the greatest impact, puts plans in place to mitigate the danger, implements those plans, then evaluates whether the risk is brought down to reasonable and appropriate levels.
The SRA and the risk management plan together serve as the foundation for compliance with the Security Rule. If you’ve performed a thorough SRA and created a comprehensive risk management plan, many later standards may be fulfilled in the process of implementing the plan and mitigating the identified risks.
A comprehensive risk management plan also serves to satisfy several HIPAA standards.
- 164.308(a)(1)(ii)(B) – Risk Management: Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with §164.306(a).
- 164.308(a)(8) – Perform a periodic technical and nontechnical evaluation, based initially upon the standards implemented under this rule and subsequently, in response to environmental or operations changes affecting the security of [ePHI], that establishes the extent to which an entity’s security policies and procedures meet the requirements of [the Security Rule].
4 Steps to Creating a Risk Management Plan

- Prioritization: The first step of analyzing the data produced in the SRA is to prioritize which risks need to be addressed immediately and which can be addressed in the future. All risk eventually needs to be dealt with, but budgets, manpower, and immediate threats will all factor into how and when.It’s vital that senior management is involved in the risk management planning process. Mitigating risk to a reasonable and appropriate level may require considerable investment of both time and money. New hardware infrastructure or outside help from IT professionals may be necessary, and employees’ time may be needed to create new policies and procedures and train staff. Even if the budget-makers aren’t involved in the SRA, having them involved in the risk management plan will help to prioritize what needs to be handled first, and allow them to see why the investment is necessary.
- Mitigation: Once the risks are prioritized, the next step is to decide how to mitigate the possible danger. Just as with the rest of HIPAA, how this happens is determined differently by each company depending on the level of risk posed and the resources available. What’s important to remember is that the goal is not to eliminate risk all together. If it’s possible to do so and still have a functioning and sustainable business, all the better, but for most businesses, the complete elimination of risk may be either too expensive or too prohibitive to actually continue fulfilling their core mission. The goal of mitigation is to reduce risk to a reasonable and appropriate level. Do all you can within your means to protect ePHI.
We cannot stress enough that while cost is one factor to consider in your mitigation strategy, it alone cannot be used to justify not mitigating risk if the likelihood of a threat and the potential impact are severe enough.
- Implementation: A comprehensive risk management plan is useless if it’s not implemented. Failure to put the new policies and procedures to safeguard ePHI into action throughout your company can result in the vulnerabilities you identified being exploited: exposing ePHI, your company losing trust, and incurring serious fines. Implementation needs to occur at all levels of your business, from documenting the newly created policies and procedures, to infrastructure investments, to checking the settings on hardware you identified as a risk. According to NIST SP 800-39,
The objective is to institutionalize risk management into the day-to-day operations as a priority and an integral part of how organizations conduct operations . . . recognizing that this is essential in order to successfully carry out [business] missions in threat-laden operational environments.
NIST is talking about IT operations, but the same is true to all threats to ePHI. A culture of avoiding or mitigating risk at every level can produce a working environment that protects ePHI and strives to maintain security measures. Remember, the risk management plan is essentially a plan of action that must be put into practice to be successful.
- Evaluation: Implementing your risk management plan won’t protect ePHI if, ultimately, the mitigation strategy you chose doesn’t work as expected. That’s why evaluating the success of your risk management plan after implementation is important. Once in place, you may find that what you thought would mitigate the risk hasn’t done so, or hasn’t done it as well as necessary to bring the danger down to reasonable and appropriate levels. Or you may find that while it does mitigate risk, it also causes severe difficulties in the day-to-day operations of your business. In these cases, another strategy may be more successful for your business in the long run.§164.308(a)(8) also requires covered entities to “perform a periodic technical and nontechnical evaluation . . . in response to environmental or operations changes . . . that establishes the extent to which an entity’s security policies and procedures meet the requirements of [the Security Rule].” This means that subsequent SRAs need to be performed and your risk management plan re-evaluated whenever there are major changes to your business or IT infrastructure that could affect ePHI. Like we mentioned in Part 3 of our HIPAA series, documentation is a constant part of compliance with the Security Rule, and the risk management plan is no different. Having a clear record of what you planned, when and how you implemented the plan, and the success or failure of those actions are necessary not only for your own future use but also in case you’re audited.
The Cycle Never Ends
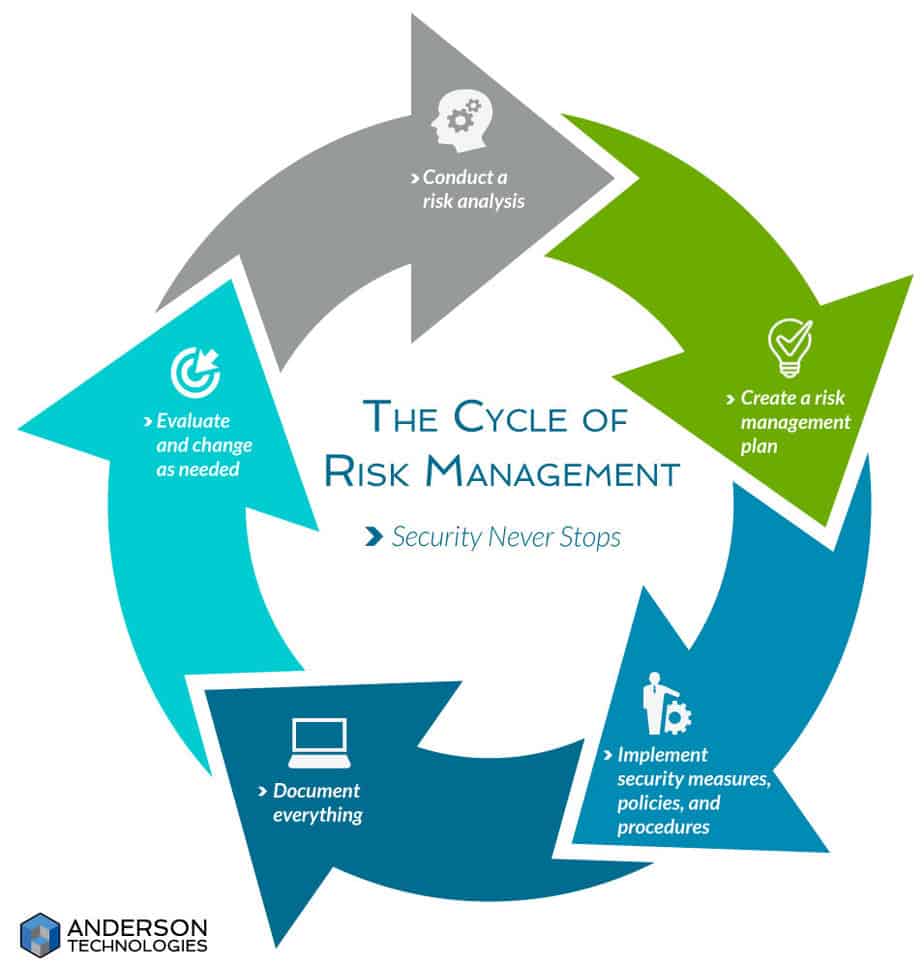
The most important thing to remember about risk is that it never ends and is always finding new ways to threaten your business. You have to keep moving right along with it. Risk management is a continuous cycle of analyzing risk, implementing a plan to fix it, determining if that plan worked, and repeating.
For some businesses, performing an SRA and updating a risk management plan might be an annual activity as part of their HIPAA compliance. Other businesses that have fewer risks and fewer changes to the business may decide to wait two or three years between SRAs. It all depends on what is reasonable and appropriate for your organization.
Just don’t stop moving through the cycle of risk management. Danger doesn’t stop changing, and neither should you.
If you need help implementing the IT requirements of your risk management plan, contact Anderson Technologies today at 314.394.3001 or email us at info@andersontech.com.




