How to Identify Phishing and BEC Email Attacks
“No matter the request, the Anderson [Technologies] staff is always helpful and agreeable. I’ve never been made to feel that my question isn’t important.”
– R.S., Community Relations Director, Senior Living Center
A Message Arrives
Maybe it is from someone within your company, someone who you trust and interact with frequently. Maybe it is from a vendor or acquaintance, someone who you don’t know well, but have no reason to doubt.
You open the message.
The communication is simple. The subject and a link in the body refer to a secure message. On the one hand, a secure message is sure to be important and urgent. You’re busy, and might be chastised if the message is ignored for too long.
On the other hand, you’ve been taught that links in email should rouse your suspicion.


Email scams are a very real threat to every user, especially business accounts. According to Kaspersky’s annual spam report, over 50% of all emails in 2020 are connected to scams like phishing and BEC (business email compromise). That’s a lot to look out for! At Anderson Technologies, we stress the importance of email protection software, user training, and education, but even in the most protected and informed environments, scams have a way of sneaking through.
If you received this message, would you click?
Let’s take a closer look at how to decide.
Examine the Sender
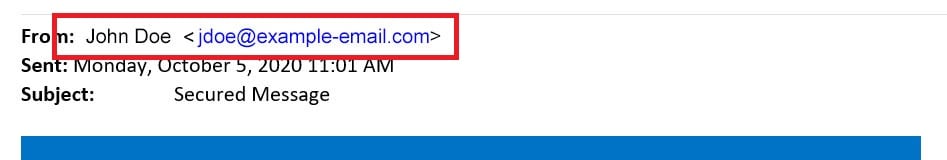
Depending on your email client, the full name and email address of the sender may or may not be immediately viewable. If you need to, click to expand the information displayed. Check that the name matches what you’d expect from this sender, and closely examine the email address for typos or gibberish.
In this case, everything looks to be on the up-and-up.
Review Graphics

If the email contains graphics such as logos or a company-specific header, don’t just rely on your memory to check accuracy and legitimacy. Have you received other messages with a similar theme? Try searching your inbox for keywords referenced. In this case, you could look for “Secured Message”.
A search engine is also your friend. The graphic logo for Office 365 looks like it could be a little bit off. Sure enough, this graphic looks like it could be based on the old 2013 version. This isn’t totally conclusive based on the search, however, so let’s keep going.
Check the Body Text
In the past, poor spelling and badly-translated grammar were often easy giveaways that a scam email was a scam. Now, email scammers often smooth out these errors. If you know the supposed sender well, however, you may still be able to identify when phrasing and certain words just don’t fit.
This email doesn’t have a lot of text to go on, but one clue that might be missed on a quick look is that the sender’s name (anonymized here) is spelled just slightly wrong.
Hover Over Links
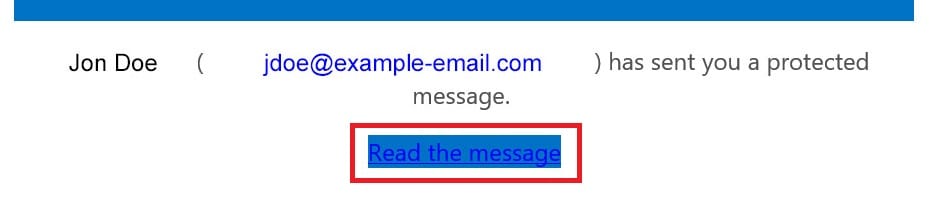
At this point we’re still not clear to click.
Hovering over the “Read the message” text displays a legitimate but unfamiliar website URL.
Instead of clicking, open a search engine and type in the root address directly. The link in this email appears to belong to a popular resource site for STEM learning tools for grade schoolers! A legitimate site, but wholly unrelated to any context for a secure message. Why would the sender route a secure message through a site with which they have no affiliation?
In other cases, hovering over the links can reveal obviously suspicious URLs (like 13hrflsdh.ru) or websites that are disguised (like rnicrosoft or micr0soft).
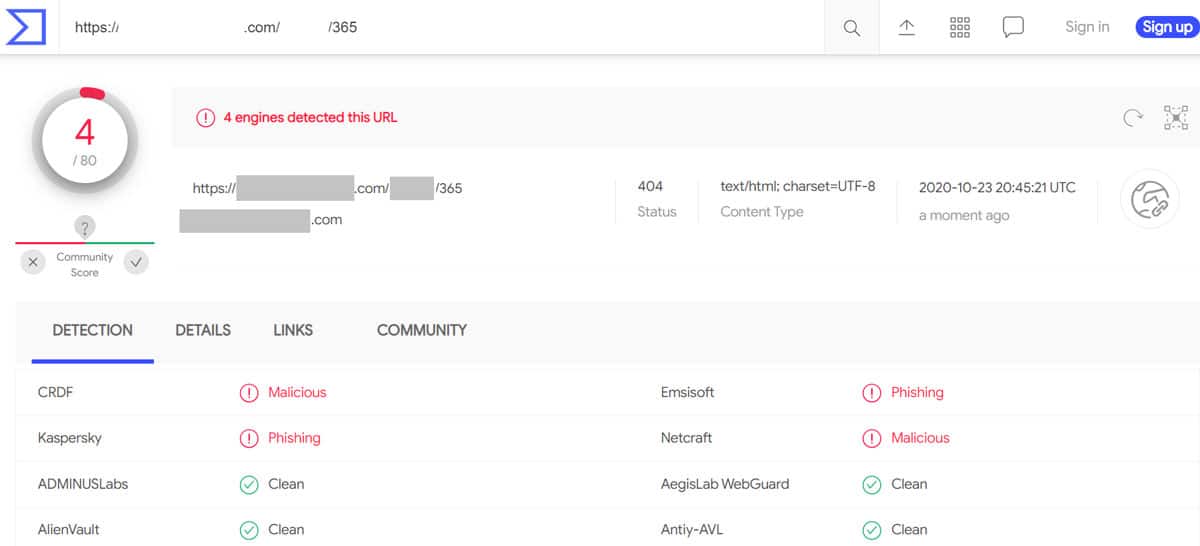
Another handy tool to utilize at this step is virustotal.com. This free service allows you to enter any URL (right click, copy URL, and paste into the tool) or file to check for suspicious content. Don’t rely solely on your email service, filtering program, or any single tool to catch phishing. A new, well-done attack can fly under the radar for hours or days.
Do Not Click!
At this point we’re still not clear to click.
Hovering over the “Read the message” text displays a legitimate but unfamiliar website URL.
Instead of clicking, open a search engine and type in the root address directly. The link in this email appears to belong to a popular resource site for STEM learning tools for grade schoolers! A legitimate site, but wholly unrelated to any context for a secure message. Why would the sender route a secure message through a site with which they have no affiliation?
In other cases, hovering over the links can reveal obviously suspicious URLs (like 13hrflsdh.ru) or websites that are disguised (like rnicrosoft or micr0soft).
Another handy tool to utilize at this step is virustotal.com. This free service allows you to enter any URL (right click, copy URL, and paste into the tool) or file to check for suspicious content. Don’t rely solely on your email service, filtering program, or any single tool to catch phishing. A new, well-done attack can fly under the radar for hours or days.
At this point, enough red flags have been raised to drop everything and forward the message to your IT team, flag it as spam/phishing, and give the sender a call to question the email, and in this case, inform them that their account has been compromised.
If you were to click, you would be taken to a mock-up of an Office 365 login page. The graphics would be a little stretched, and the logo not quite right. If you did enter your login information on this page, you wouldn’t be taken to a secure message, but you WOULD have just handed your login and password to criminals, who would then repeat this scam with outgoing messages from your own account, putting all of your contacts at risk of the same fate.
Got Questions About Email Scams? We’ve Got Answers!
419 scam/advance-fee scam: Made famous in the earlier days of email with messages from faux-Nigerian princes. This scam promises a large payout in exchange for an up-front payment. The criminal claims that they have access to a large amount of money, but need your help to access it, and in exchange for your help, you’ll be rewarded. Payments are requested in the form of irreversible transfers through wire transfer like Western Union, cryptocurrency like Bitcoin, or anonymized purchases like bulk gift cards. Once this money is sent, it is gone, and you won’t receive any promised payment.
Romance scam: The ultimate catfish. This long-con starts with generically appealing dating profiles and messages. When a potential victim reaches out, the criminal (and often, their team) spend hours plugging scripted responses into chat, email, and even phone calls. Then, months into the faked relationship, the criminal presents a problem. Perhaps they’ve lost their job and need emergency funds to pay rent. Maybe they got stranded in their travels, were robbed, and need help getting home. The initial monetary request could start out small, or the first hit could be for everything in the victim’s savings account. Often the criminal will continue to prey on a romance victim until they finally become suspicious or the source of funds dries up.
Phishing: We’ve talked a lot about phishing on our blog and website, and it is never too soon for a refresher. Think you’re a phishing expert? Take our quiz and see if you can find the reasons these emails are safe or scary.
BEC (Business Email Compromise): When directed at corporate or organizational accounts, phishing and other scams are referred to as BEC scams. The goal of BEC scams is to receive information, account credentials, and money on a scale larger than individual targets could provide.
While BEC scams are often long-term, highly targeted scams that involve masquerading as vendors or high-level employees requesting (and receiving!) wire transfers of large amounts of money, the criminals who engage in mass-email phishing attempts are the same criminals who engage in romance schemes, business espionage, and classically-known BEC scams. This results in aspects of other scams frequently appearing across the board.
Information gained in lower level attacks is used to ramp up and hone in on higher dollar targets. One stolen password may not correspond to a direct attack to the user, but that stolen password (and the information gained from the compromised account) could result in millions of dollars lost from that user’s employer years later.
Part of what makes this particular email so interesting is that it showcases just how multiple attack victims (likely accumulated by the cybercriminals over time and gained through different scams, phishes, and attacks) can be used to build bigger and more successful attacks. It is also part of a late-2020 trend: Microsoft is the most frequently mimicked brand in phishing attacks.
The resolution to this story is mixed.

Many users clicked to access their “Secure Message” and provided their login information to criminals. Not only was the sender’s account information stolen and used for the criminal’s own ends, but clearly the criminal (and their team) also performed a similar attack on the STEM site’s personnel to gain access to their website’s backend, and without alerting them, created the fake login honeypot.
The URL was eventually flagged for phishing and malicious activity, and many browsers now block access to that address, preventing further use of that particular trap. The client who encountered the phish had passwords reset by the Anderson Technologies team and their accounts remain closely monitored.
But the question remains: Would you click?
Cyber and email security training is a key part of any organization’s IT. Interested in scheduling a training session, or assessing solutions that can augment email safety? Take the time to build solutions and safety nets before a breach.
A Free IT Assessment Can Help You Identify Risks
Your organization is too valuable to not have modern IT systems to keep it safe and make it scalable. A free Anderson Technologies IT Assessment will identify where you are the most vulnerable and recommend the areas to address first, affording you the most protection and peace of mind.




