Sitting on a Powder Keg: What CEOs Must Address in Their IT Landscape – Part Four
By Farica Chang, Managing Principal “Don’t click on suspicious links.” If that’s the extent of your company’s cybersecurity training, you might as well tell your employees not to get scammed. The truth is, while your IT team has been repeating the same cautionary tales, cybercriminals have been engineering increasingly sophisticated attacks that exploit our inherent […]
Sitting on a Powder Keg: What CEOs Must Address in Their IT Landscape – Part Three

By Farica Chang, Managing Principal Key in the right combination of letters in May 2016, and you could’ve gained access to the Twitter, Instagram, and Pinterest accounts of one of the founding fathers of social media. Turns out, even Mark Zuckerberg wasn’t safe from account compromise—or the consequences of not enforcing strong access controls. By […]
Sitting on a Powder Keg: What CEOs Must Address in Their IT Landscape – Part Two

By Farica Chang, Managing Principal What would you consider your IT team’s most important responsibility? Fixing a Wi-Fi outage, perhaps? Setting up accounts so your new hires can hit the ground running? Or maybe the password resets that save your staff time and time again. If you asked any of our team the same question, […]
Seasonal Safety: How to Avoid Cyber Scams This Festive Season

By Amy Anderson, Founding Principal The holiday shopping season is upon us, and while you’re making your list and checking it twice, cybercriminals are crafting their own strategies to separate you from your hard-earned money. Today, we’re providing some guidance on staying safe during the festive period—and all year round. Key Insights The promise of […]
Cyber Spoofing, Imitation, and Scams… Our Own Experience

By Mark Anderson, Founding Principal In the world of AI, digital-first, and social media, anyone can be impersonated or spoofed… even us. Learn about a new kind of cyber scam and how perpetrators are using legitimate businesses to try and validate their activities. There are many types of cybercrime and cyberattacks happening every day online. […]
5 Highly Effective Habits to Keep You Cybersecure this October

October marks Cybersecurity Awareness Month, and while every month should focus on cybersecurity (in our humble opinion), there’s no better time to strengthen your business’s defenses. These days, any individual or organization can be a target, which means developing strong cybersecurity habits is crucial for safeguarding your company’s data and operations. No matter your technical […]
Protect Your Castle: A Multi-Layered Cybersecurity Defense Strategy
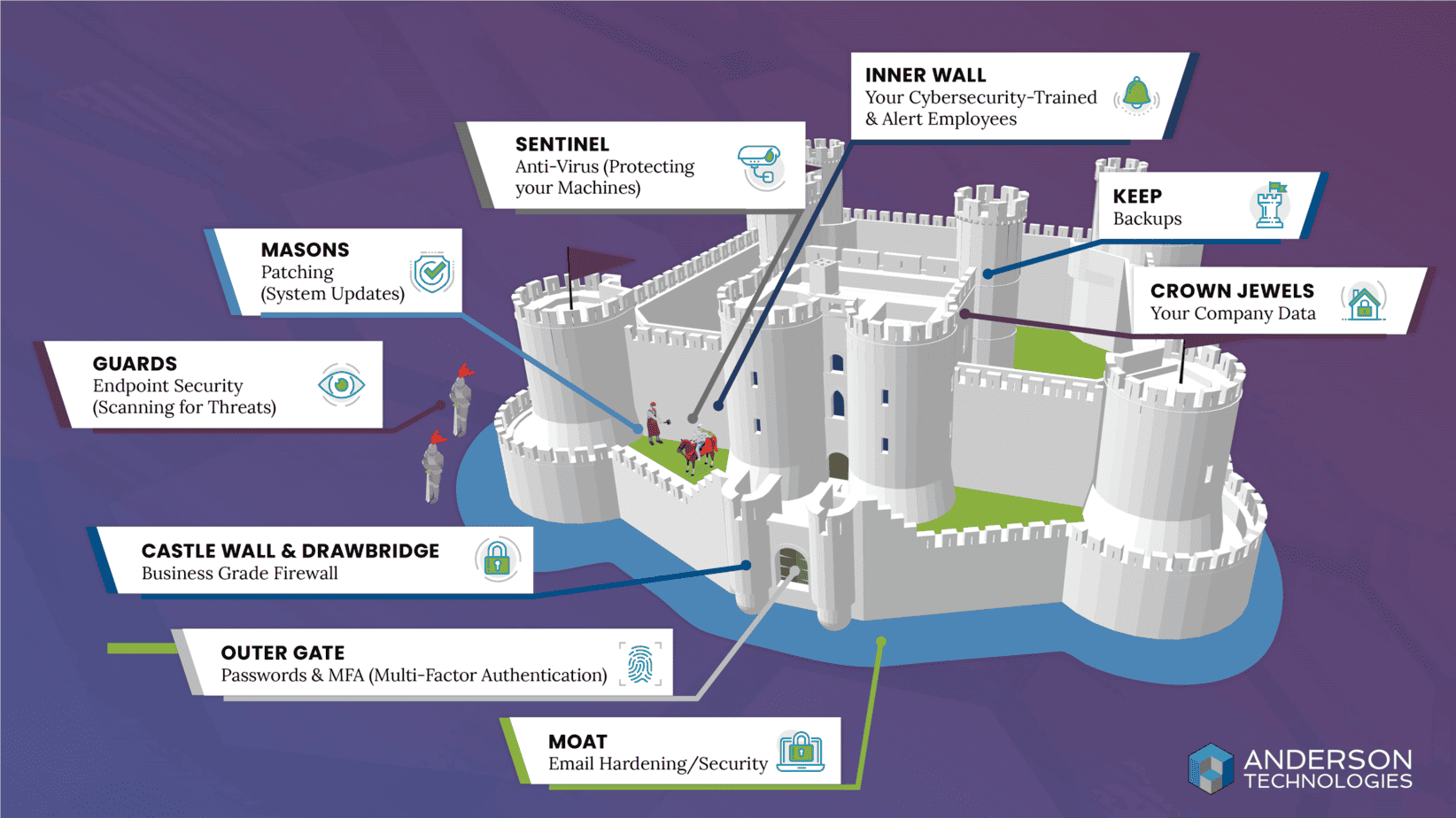
By Managing Principal Farica Chang Imagine your business as a majestic castle, standing tall on a hill. Its walls, moat, and towers protect the treasures within—the data, systems, and sensitive information that keep your organization running smoothly. Just like a castle, your IT infrastructure relies on layers of defense to thwart cyber threats. Mark Anderson […]
Are You Ready for SEC Rule 10?

Public and private companies in the financial services industry face an ever-growing number of external influences and pressures around good business practice and regulation. Two of the most critical are the mounting expectations to keep people and data safe and the scrutiny of regulators that exist to protect the assets of the industry. The SEC […]
10 Reasons Why You Shouldn’t Switch Your IT Support Provider

Companies like yours often stick with their IT support provider for many years, and it can take something quite substantial to prompt them to consider making the switch, even though there may be many small things telling you that it is time. Making the leap to a new IT provider can feel daunting, risky, and […]
Navigating Deceptive Impersonation Scams

Equipped with tactics that play on trust and urgency, scammers around the world have one goal in mind: to deceive you out of your hard-earned money. A particularly insidious method in their toolkit is the impersonation scam, where these criminals camouflage their intentions with a cloak of legitimacy. There are many ways impersonation can be […]



